Pegasus works on phones running Android, BlackBerry OS, and iOS operating software. (Reuters)
Electronic devices infected with Pegasus, a notorious spyware program sold only to governments, have been discovered in South Africa. The spyware, developed by Israeli cyber warfare firm NSO Group, has been used to target journalists and human rights activists across the world.
In a report titled ‘Hide and Seek’ which was released on Monday, Citizen Lab — a Canada based internet watchdog — identified 45 countries in which infected devices have been traced, after scanning the internet for servers associated with Pegasus spyware. It also identified multiple instances of cross-border surveillance.
Twelve African countries, including South Africa, are on the list. The others are: Algeria, Côte d’Ivoire, Egypt, Kenya, Libya, Morocco, Rwanda, Togo, Tunisia, Uganda and Zambia.
In a statement to Citizen Lab, NSO Group said: “Our product is licensed to government and law enforcement agencies for the sole purpose of investigating and preventing crime and terror. Our business is conducted in strict compliance with applicable export control laws.” It added that there are “multiple problems” with the Citizen Lab report, and that the list of 45 countries is inaccurate.
In response to the report, the Committee to Protect Journalists, an non-governmental organisation advocating for the rights of journalists, issued a safety advisory: “The spyware gives the attacker the ability to monitor, record, and collect existing and future data from the phone. This includes calls and information from messaging applications and real-time location data. The spyware is able to remotely activate the camera and microphone to surveil the target and their surroundings … Journalists will likely only know if their phone has been infected if the device is inspected by a tech expert.”
Pegasus works on phones running Android, BlackBerry OS, and iOS operating software. It can be installed simply by clicking on a link, which is often designed to look like a message from a source or a breaking news story.
In the Columbia Journalism Review, Avi Ascher-Shapiro, a New York-based technology and foreign affairs journalist said, “The threat this poses to journalists can’t be overstated: A Pegasus operator can quietly transform a cellphone into a surveillance hub, tracking the reporters movements, identify sources, even potentially impersonate that journalist in the digital world.”
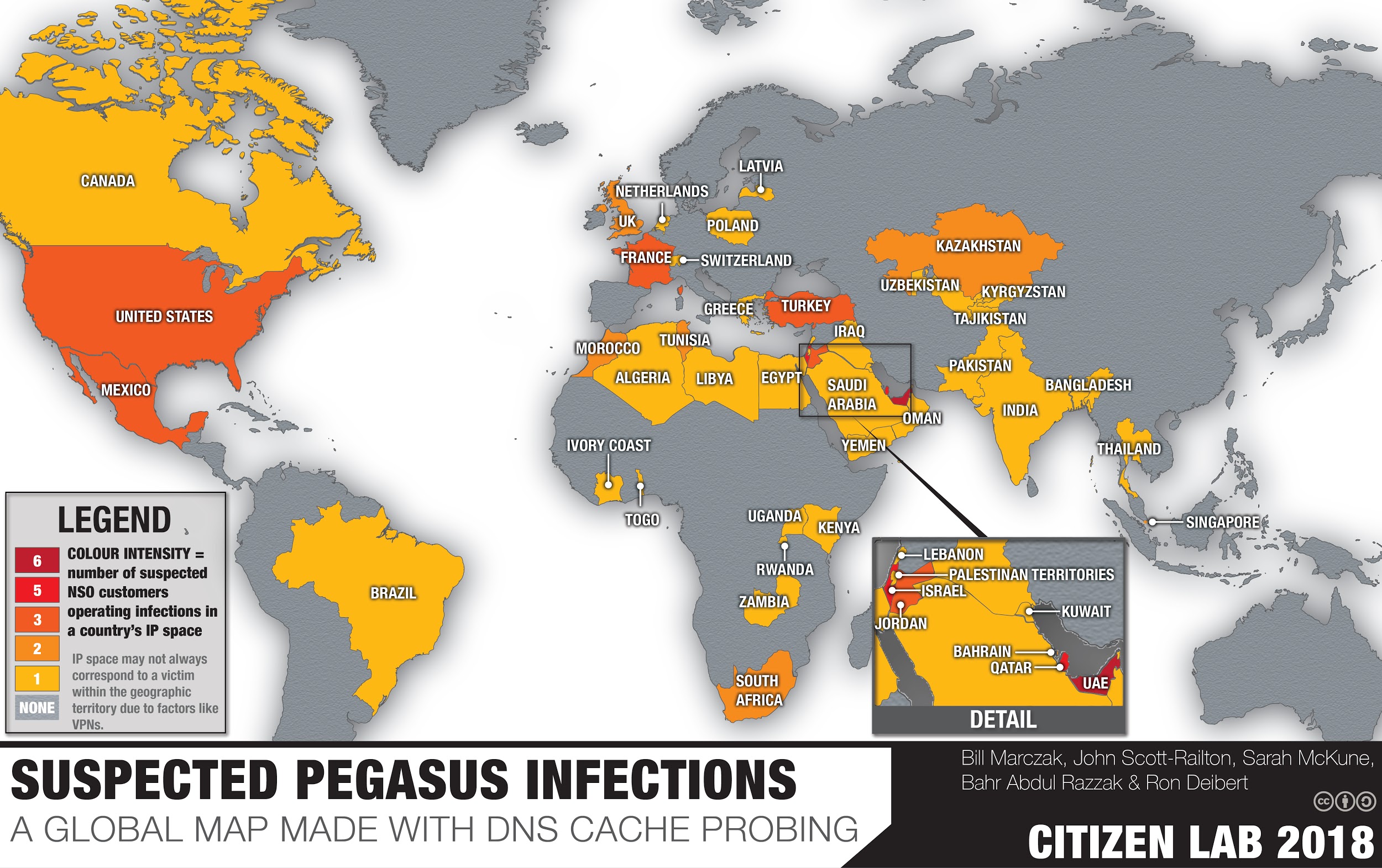
Global map of suspected NSO Pegasus infections. (Image via Citizen Lab)
In its report, the Citizen Lab said that it had identified several operators of Pegasus that seem to be targeting African countries. “We identify five operators focusing on Africa, including one that appears to be predominantly focusing on the West African country of Togo, a staunch Israel ally whose long-serving President has employed torture and excessive force against peaceful opposition. The operator in Togo may have used websites with names like “nouveau president” (“new president”) and “politiques infos” (“political information”) to infect targets with spyware. A separate operator that appears to focus on Morocco may also be spying on targets in other countries including Algeria, France, and Tunisia.”
The Mail & Guardian has reached out South Africa’s ministry of state security for comment.